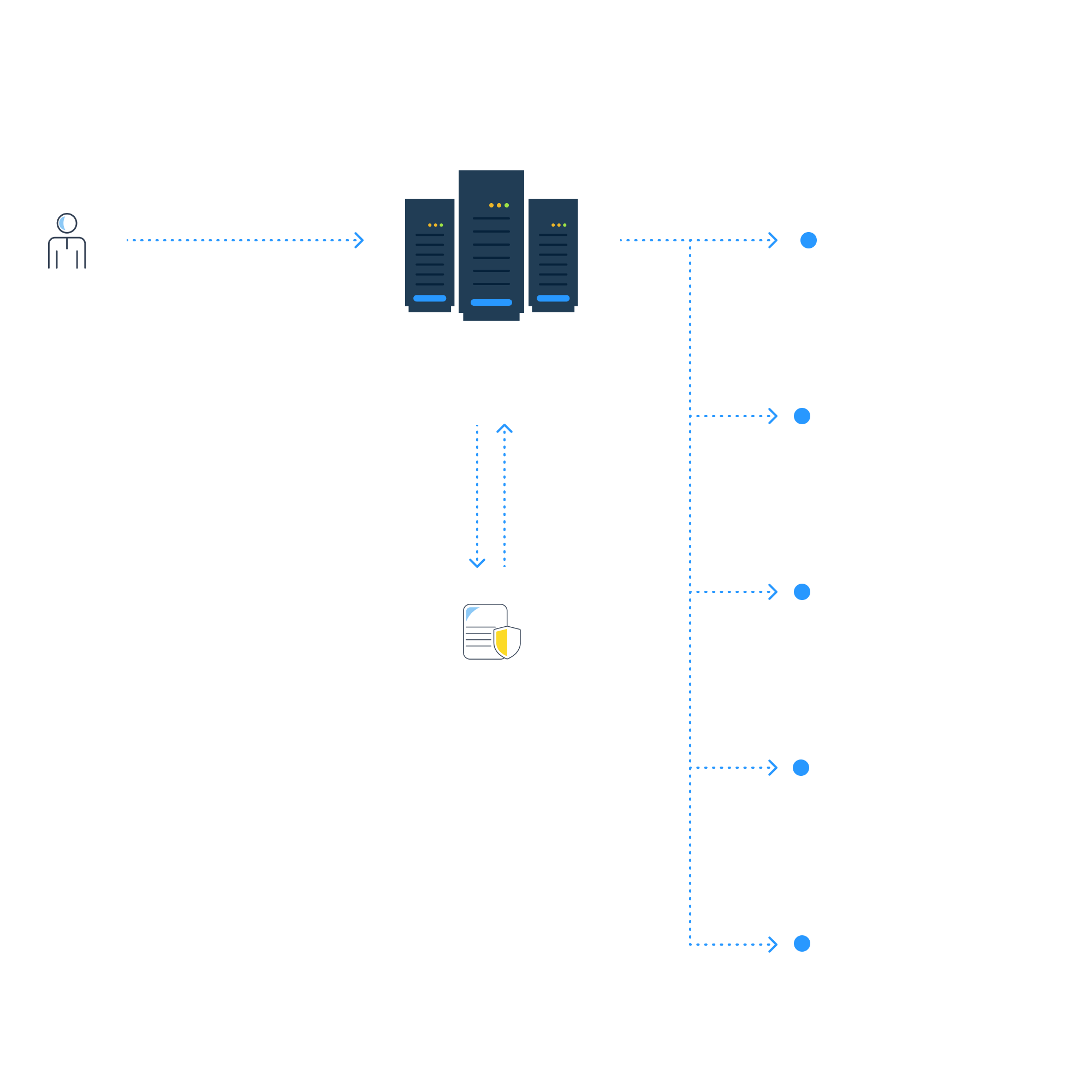
Customer Identity Management Capabilities
API Access Control
Why API access control capabilities matter for better customer identity management.
For your customer
“If an app takes me to another app, I still expect that my information and transactions are safe and secure.”
For your company
“We need to ensure we protect our customers for every application and service that uses their personal information.”
Related Resources
REPORT
Customer Identity Management Overview
REPORT