I’ve spent most of my career either going into an M&A event, sitting in the middle of an event, or coming out the other side of one. If you’ve spent more than a decade in the IT industry, you’ve likely experienced this yourself as an employee of the companies involved, or as a customer of them.
Due to this, if you’re like many organizations, you’re likely saddled with multiple IAM systems in your technology ecosystem. In fact, our 2024 State of Authentication report showed that a whopping 76% of the 200+ enterprises surveyed have multiple IdPs. The reasons are varied, but as your organization scales, this proliferation of technology often leads to unintended consequences—security gaps, inconsistent user experiences, and bloated IT budgets.
While multiple IAM systems may seem like a solution, they often create more problems than they solve.
The Hidden Risks of Tech Sprawl in IAM
You might think that more IAM tools are necessary, but they come with hidden risks. Each tool operates on its own protocols, making it nearly impossible to unify security policies across your organization. This fragmented infrastructure creates gaps that bad actors can easily exploit.
Your IT teams end up spending more time managing these disparate systems, and the increased complexity drains your resources. You also expose your organization to inefficiencies and greater security risks.
How Multiple IAM Systems Impact Security and User Experience
When you rely on multiple IAM solutions, the user experience often takes the hit first. Your employees deal with multiple logins, conflicting password policies, and varied MFA prompts. These frustrations don’t just inconvenience your users—they push them toward risky workarounds like password reuse.
Identity sprawl becomes a major vulnerability. Fragmented systems fail to provide consistent user authentication, and attackers know how to exploit these weaknesses.
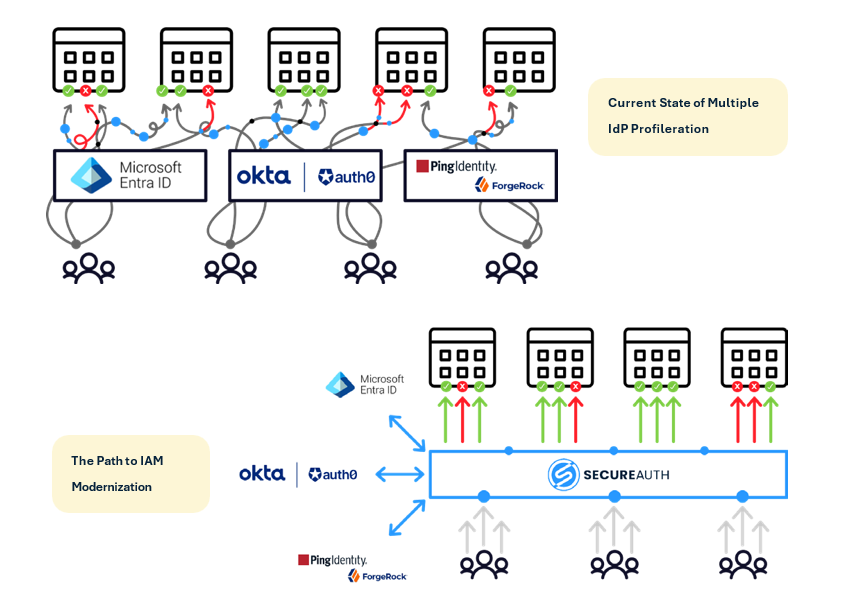
Consolidation: The Key to Securing Your IAM Strategy
Adding more tools isn’t the answer. The real solution is to consolidate and streamline your IAM approach. SecureAuth’s platform integrates key components like SSO, MFA, and Federation into one unified system. By centralizing your IAM, you reduce complexity, lower operational costs, and strengthen your security.
Get Ahead of the Problem
The longer you spend managing multiple IAM systems, the more vulnerabilities you introduce. Consolidating your tech stack strengthens security, enhances the user experience, and reduces IT overhead.
Stop Letting Technology Sprawl Hold You Back
Excessive IAM tools create chaos and security risks. A streamlined approach lets you regain control over your environment. Simplify your IAM strategy for improved security and efficiency.
Download our ebook, Tackling 3 of IAM’s Biggest Challenges, and start your journey toward a more secure, cohesive IAM environment.
