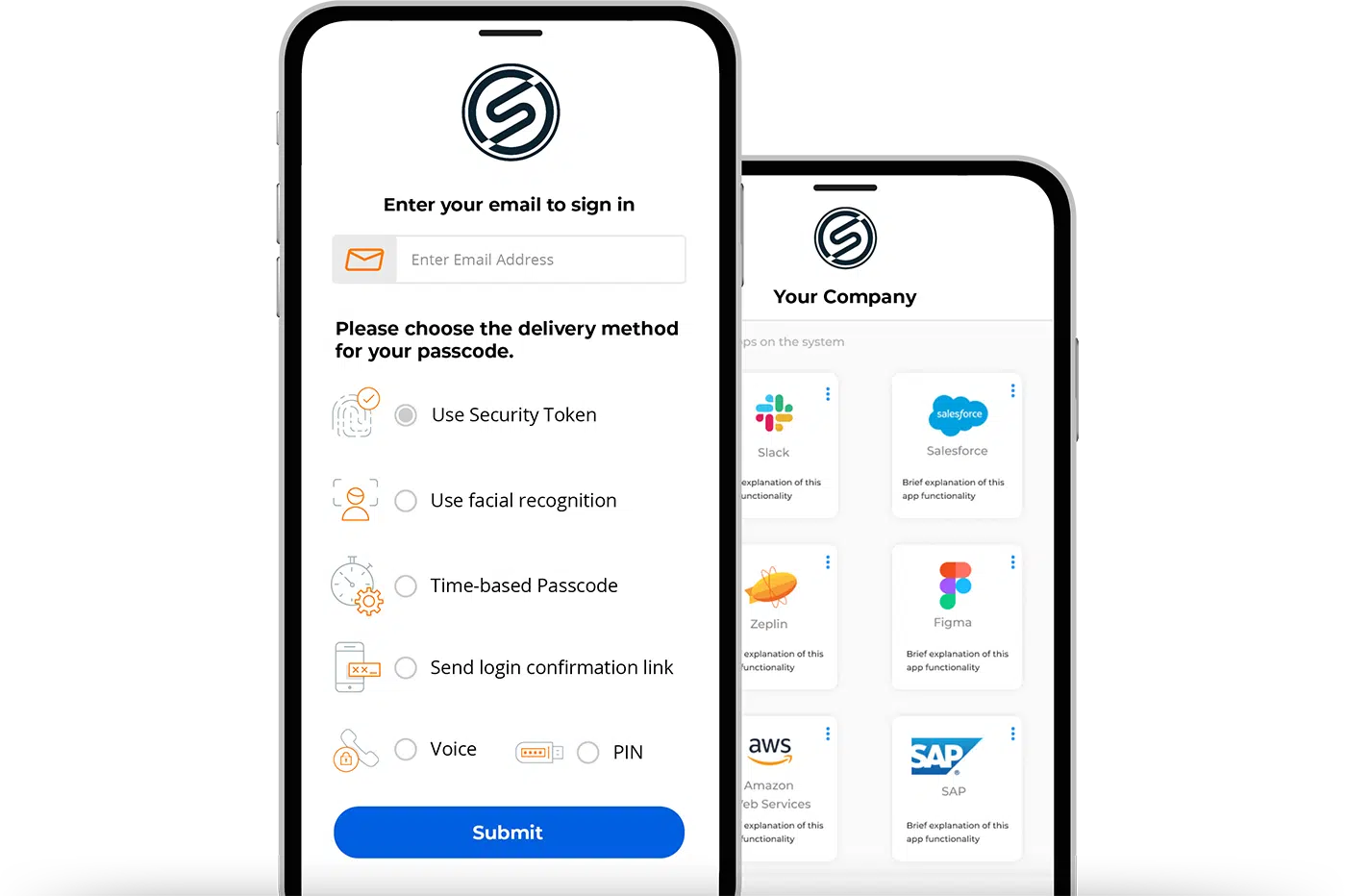
Workforce Identity Management Capabilities
Multi-Factor Authentication
Why multi-factor authentication capabilities matter for better workforce identity management.
For your employee
“The process of logging in with MFA is straightforward and doesn’t add much time to my day. I use an authentication app on my phone, and the setup was quick and easy.”
For your company
“Knowing there's an additional layer of protection beyond just a password gives me peace of mind. It means that even if a password is compromised, unauthorized access to our systems is still extremely difficult.”
Related Resources
ARTICLE
Tackling MFA Challenges and Identity Threats with SecureAuth’s Passwordless Continuous Authentication and Authorization
REPORT
Workforce Identity Management Overview
REPORT